Were there early warnings that BA was being attacked? We look at 2 potential scenarios that led to the hack.
Were there early warnings that BA was being attacked? We look at 2 potential scenarios that led to the hack.
*Updated September 13th*
British Airways, the UK’s flagship airline has been hit by a major cyber attack. According to CEO Alex Cruz, the company was recently hit with a “sophisticated, malicious criminal attack” on its website which has affected 380,000 transactions.
The company says “customer bookings made or changed between 22:58 BST August 21 2018 and 21:45 September 5 2018 inclusive” were affected and “the personal and financial details of customers making or changing bookings on ba.com and the airline’s mobile app were compromised. No passport or travel details were stolen.”
What we don’t know yet is how this attack was carried out or who is behind it. Looking from the outside in however, there are some indicators which can shed more light on the situation.
An Early Warning?
A few weeks ago, the DynaRisk intelligence team found a cyber criminal selling British Airways Avios points on an underground market at a rate of £20 per 30,000 points. Assuming 1 point is worth 1p, each £20 transaction could be worth £300. The most recent transaction took place on August 11th, 10 days before the hack occurred.
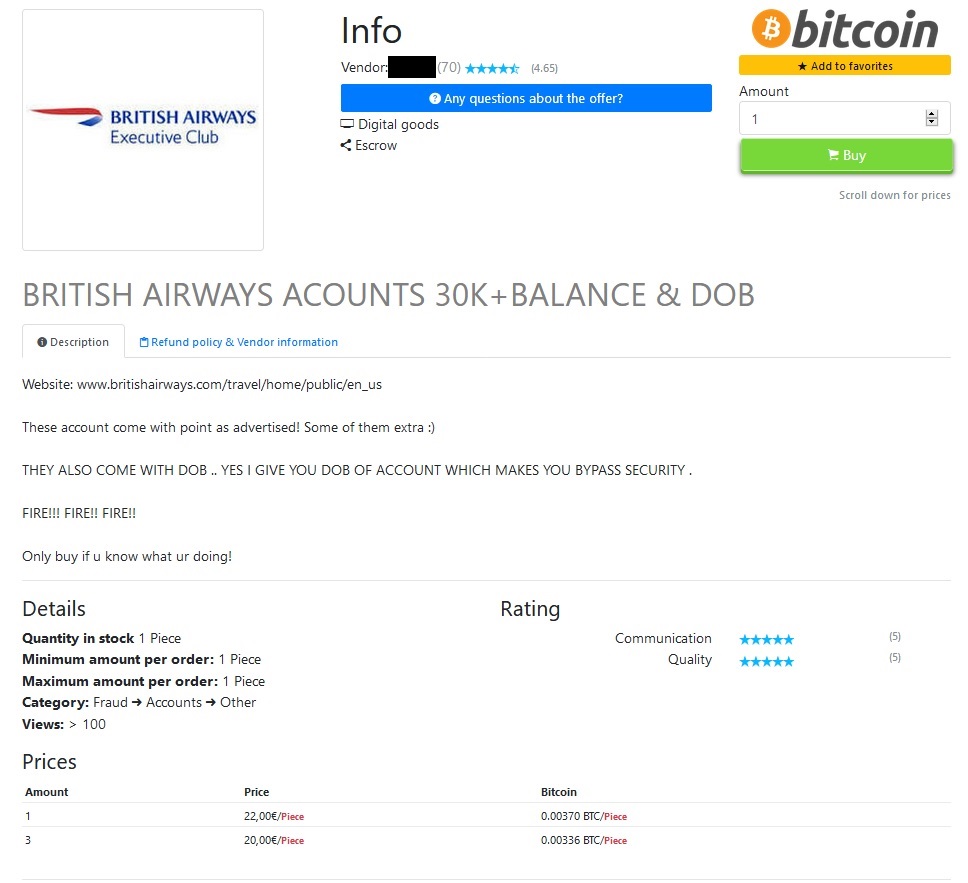
A cyber criminal advertising BA avios poits for sale.
Fast forward to September 7th and the advertisement has changed, the seller is now offering minimum transfers of 100,000 points or more for $850. According to the ad, the seller reportedly can “make an account for you with miles included”. The question is, how could the seller make an account on a BA computer system? They would need to have compromised one of BA’s systems or administrative accounts to do it.
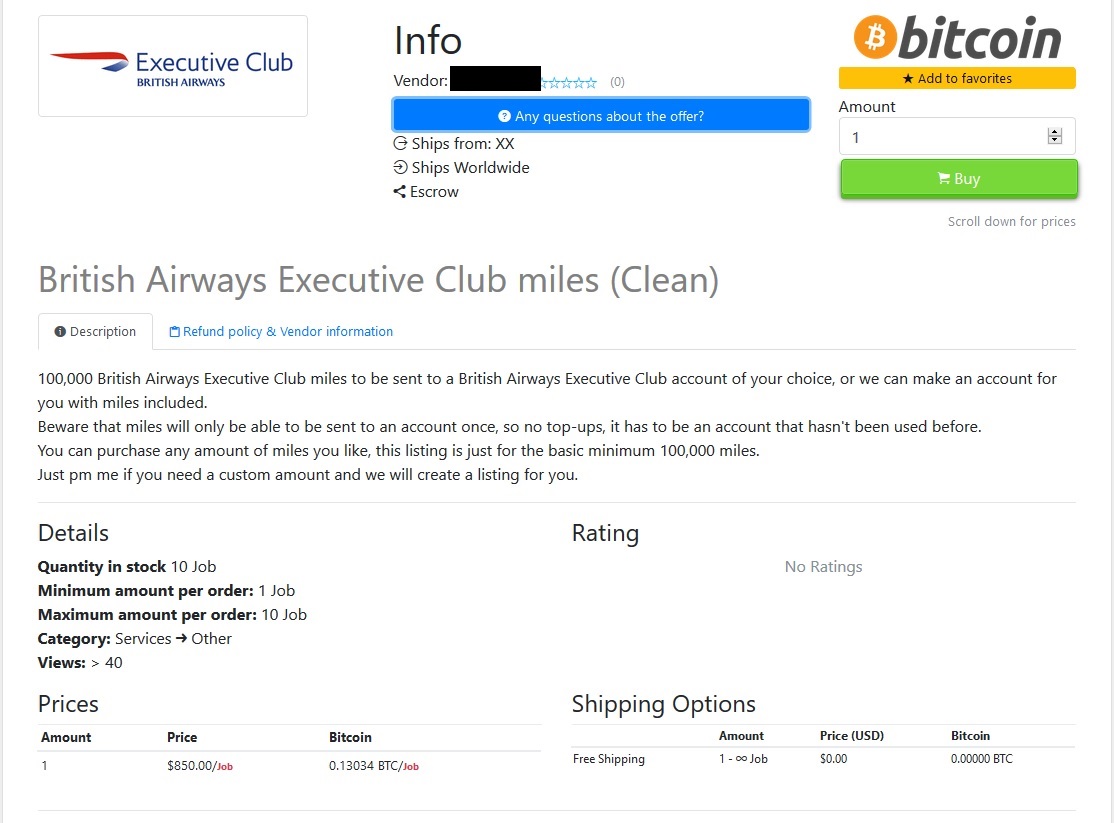
Scenario 1 – Administrative account takeover
DynaRisk has obtained billions of pieces of data from the Dark Web so we checked to see if BA staff had information stolen in other data breaches. Cyber criminals use stolen data, like passwords, from other hacks to take over a person’s accounts and infiltrate companies.
According to our records, over 3,000 BA corporate email accounts have been exposed a total of over 8,400 times in 45 separate data breaches from over the years. BA has done nothing wrong, they have unfortunately just gotten caught up in other hacks that affected companies like LinkedIn, Adobe, Dropbox, Forbes, Edmodo and others. In these attacks, hackers have stolen passwords for BA accounts which might have still been in use somewhere.
Just about any medium to large size company will have had accounts exposed in data breaches. In fact over 60% of individuals have had their information stolen in at least one data breach.
Scenario 2 – Recently disclosed web server flaw
On August 22nd, a vulnerability was published for a component of the Apache web server, called Struts. This is a newer flaw in the same software component that was hacked by criminals in the Equifax data breach.
While it is difficult to check the British Airways website for this specific flaw externally, using a simple check we can see that www.britishairways.com does in fact run the Apache web server.
HTTP/1.1 200 OK
Server: Apache
Social media also provides some circumstantial evidence to support this scenario as several BA engineering employees reference Apache Struts as a skill on their public LinkedIn profiles.
Chris Wallis, Founder & CEO of Intruder, a website security scanning company, said “While it’s not possible to say whether BA were using the Struts component on their site, if they were it could have provided a very easy way for attackers to gain access. The weakness affected every single website using Struts and gives the attacker full access. In this scenario though most companies would have found it difficult to patch the weakness in such short timescales, and only detecting the weakness as fast as possible would have helped them achieve that.”
Attacks On Airlines & Supply Chain
It would seem that a group of cyber criminals may be actively targeting the airline industry with Air Canada experiencing a breach on August 22nd affecting 20,000 customers and Virgin America getting hit by an attack as well.
Cyber criminals may also be targeting the small business supply chain that supports them with a recent example of a data breach affecting Delta Airlines from one of its suppliers.
Financial services companies have invested heavily in cyber security controls in recent years, perhaps airlines and their supply chains are just catching up.
British Airway’s Response
While a huge negative reaction to the news has erupted on social media, the fact is BA is handling this data breach well at this stage. The company and it’s CEO have been quick to admit the breach and notify their users and the public. While some BA customers have complained that they haven’t yet received letters from BA with details of the breach, the fact is before the new GDPR went into effect, it could have been months before customers were notified.
*Update September 13*
New details have recently emerged that another cyber security company, Risk IQ, has found that 22 lines of code were inserted into one of BA’s websites which would “skim” credit card details from victims before they clicked the submit button.
This demonstrates that BA was specifically targeted by very sophisticated threat actors who knew what they were doing. Risk IQ links this attack to a group they have dubbed “Magecart”.
The fact remains that we still do not yet know how this malicious code was inserted into the BA website and mobile app. The criminals could have used several methods of gaining access to BA servers including the 2 methods described above.
BA customers have now started receiving 1 year free ID theft monitor services which claims to reduce a person’s risk of fraud and ID theft.
The problems with ID Theft monitoring
While it is great that BA is providing some level of assistance to customers who have been affected by the breach, the fact is that ID theft monitoring services are very limited.
These services are very reactive, they tend to kick in when something has already happened like a new loan being taken out in your name.Many times fraud occurs without anyone touching your credit file, here are a few examples:
-A stolen credit card is used online somewhere else, goods are purchased in your name then shipped to the criminal
-You get tricked into sending a high value bank transfer to the wrong account
-A criminal takes over your email account and impersonates you
-You get a virus on your PC which steals your data or holds it for ransom
-You get sent an extortion email to scam you out of thousands
For those who are frustrated with BA’s security and want to do more to protect themselves, we’ve created a special 20% off coupon for our DynaRisk Pro plan.
Sign up here for a free trial and apply coupon code BABREACH to get your exclusive discount which is valid until September 30th.
